Trust the person
behind the device
Secure digital interactions with behavioral
and device insights
Trust the person behind the device
Secure digital interactions with behavioral and device insights
Trust the person
behind the device
Secure digital interactions with
behavioral and device insights
Security without
the friction
By leveraging our unique behavioral and device insights, you get better risk scores and improve your user experience from login to logout. It’s that simple.
Security without the friction
By leveraging our unique behavioral and device insights, you get better risk scores and improve your user experience from login to logout. It’s that simple.



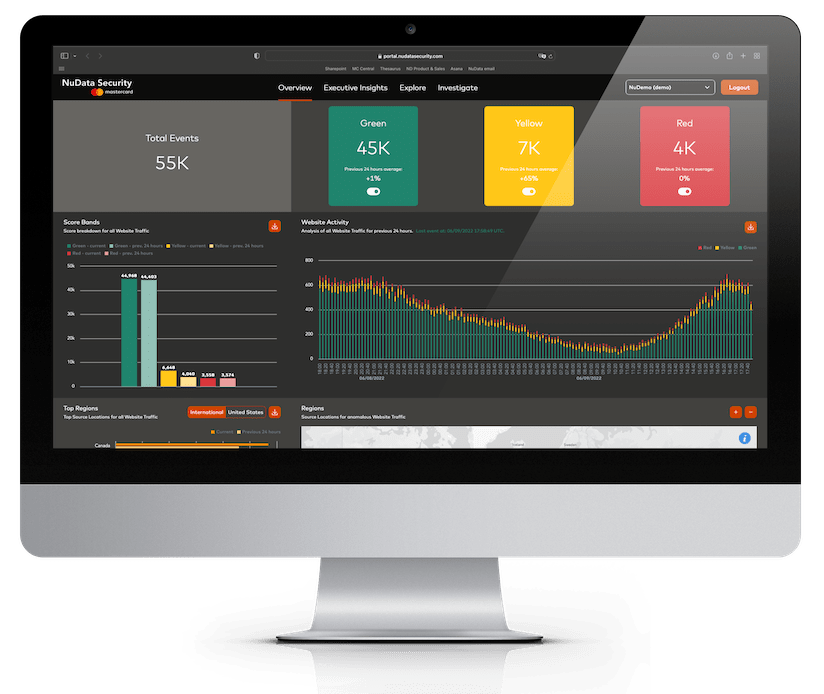
A solution for every challenge
Results in numbers
+20B
risk assessments
every year
4.5B
devices monitored
every year
3.4B
accounts protected
every year
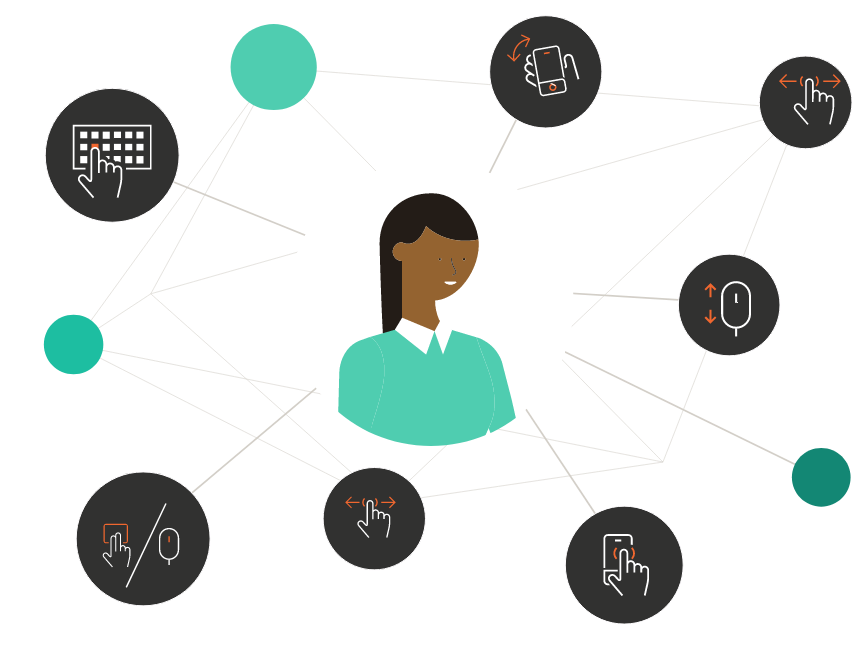
An unmatched product
NuDetect combines behavioral signals, device intelligence, and an unparalleled trust network to separate good from bad traffic passively and in real time.
An unmatched product
NuDetect combines behavioral signals, device intelligence, and an unparalleled trust network to separate good from bad traffic passively and in real time.